Introduction to End-to-End Visibility
End-to-end visibility plays an important role in modern observability by enabling
organizations to monitor and understand their entire IT infrastructure and application. By gaining an overall view of their systems, businesses can quickly identify and resolve issues.This optimizes performance, and ensures easy user experiences. This blog insights you into the importance of end-to-end visibility, key components and best practices, the tools and technologies that helps to achieve it, and real-world applications demonstrating its impact.
Importance of Overall Observability
Overall observability is essential for maintaining the health and performance of complex IT
environments. End-to-end visibility ensures that all components, from infrastructure to
applications are monitored continuously, providing insights that help as follows:
◈ Early detection of Issues: Detecting problems before they cause critical failures.
◈ Optimizing Performance: Ensure optimal performance of applications and services by identifying bottlenecks and resource constraints.
◈ Enhancing Security: Monitor for unusual activities and potential security breaches across the entire environment.
◈ Ensuring Compliance: Maintain compliance with industry standards and regulations by providing detailed logs and metrics.
Key Components and Best Practices
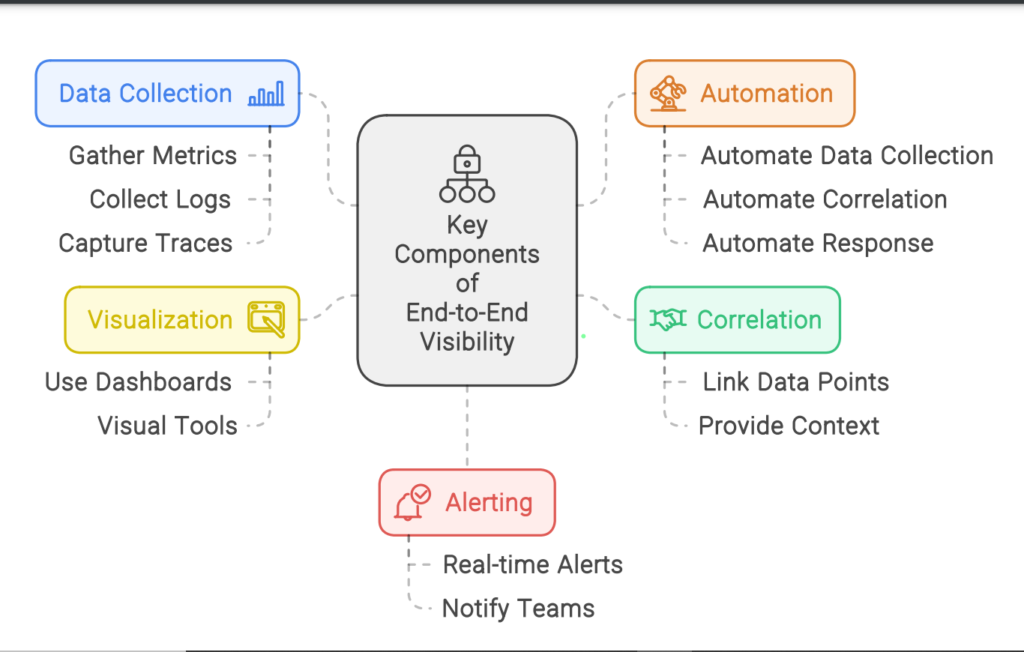
Key Components
2. Correlation: Link the related data points from different sources to provide context and comprehensive insights.
3. Visualization: Use dashboards and visual tools to present data in an understandable and quick actionable format.
4.Alerting: Implement real-time alerts to notify relevant teams of potential issues at the earliest.
5. Automation: Automate data collection, correlation, and response to streamline observability processes.
Best Practices
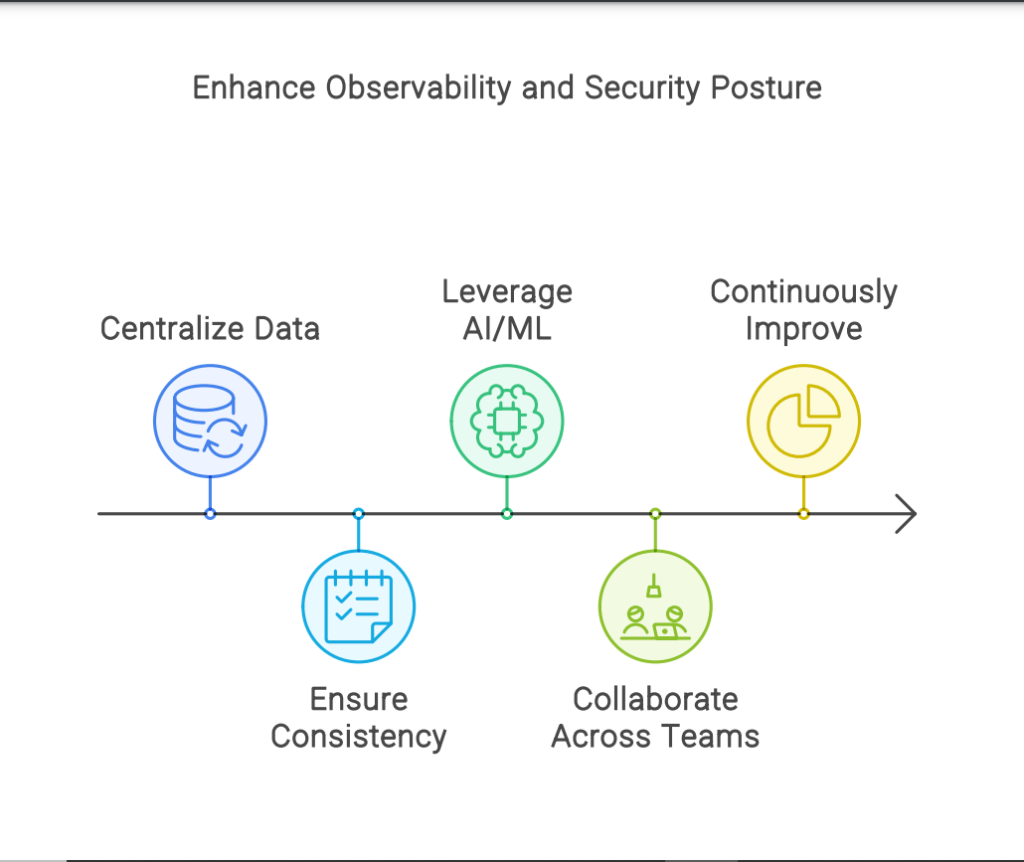
◈Centralize Data:Use one platform to collect and analyze data from various sources
◈Ensure Consistency: Standardize logging practices and data formats across the
organization
◈Leverage AI/ML: Utilize artificial intelligence and machine learning to identify patterns and
predict crucial/potential issues.
◈Collaboration: Collaboration between development, operations, and security teams to
ensure comprehensive visibility.
◈Continuously Improve: Regularly review and update observability practices to adapt to
changing environments and technologies.
Technologies for Achieving End-to-End Visibility
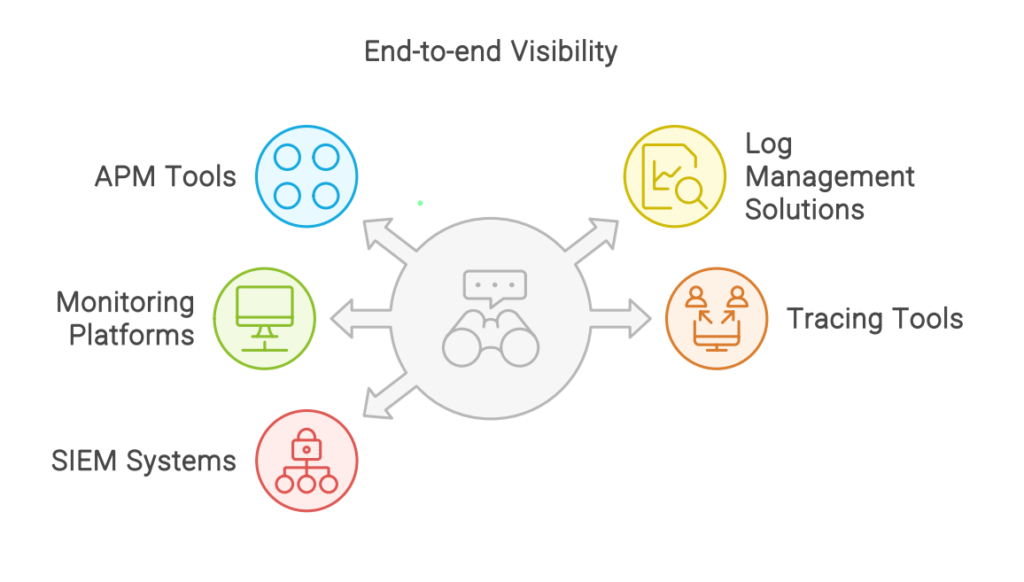
Below are the technologies included in Observelite to achieve end-to-end visibility:
APM (Application Performance Management) Tools: They provide detailed insights into
how applications are performing, tracking key metrics like response times, error rates, and
throughput. APM tools help identify and diagnose performance issues, understand user
experiences, and optimize application performance.
Log Management Solutions: Log management solutions aggregate, analyze, and visualize
log data generated by applications, servers, and network devices. These tools are crucial for
troubleshooting issues, ensuring security, and maintaining compliance. They help in
identifying patterns, detecting anomalies, and gaining actionable insights from logs.
Monitoring Platforms: Monitoring platforms continuously track the health and performance
of IT infrastructure and applications. They provide real-time visibility into system metrics,
application performance, and network status, offering alerting and reporting capabilities.
Tracing Tools: Tracing tools enable distributed tracing, which tracks the flow of requests
across different services in a microservices architecture. This helps in understanding how
different services interact, identifying bottlenecks, and diagnosing latency issues.
Security Information and event management (SIEM) Systems: SIEM systems provide overall;
visibility into security events and potential threats by aggregating and analyzing security data
from various sources.
They offer real-time monitoring, event correlation, and automated incident response to help
detect and respond to security incidents.
Real-World Applications
Financial Services
A global financial institution has huge data from multiple sources, hence they have to use
end-to-end visibility to monitor transaction flows, ensuring that all transactions are processed
efficiently and securely. By correlating data from various systems, they can quickly detect and
resolve issues, minimizing downtime and maintaining customer trust.
E-commerce
Healthcare
A healthcare provider has uses end-to-end visibility to ensure the reliability and security of
their electronic health record (EHR) systems. By continuously monitoring their IT
infrastructure, they can prevent disruptions that could impact patient care and maintain
compliance with healthcare regulations.
Conclusion and Call to Action
Achieving end-to-end visibility is the base of effective observability, providing the insights
needed to maintain and optimize complex IT environments. By implementing the right tool
like Observelite, technologies, and best practices, organizations can ensure comprehensive
observability, enhance performance, and improve security. Start your journey towards
end-to-end visibility today to unlock the full potential of your IT infrastructure and deliver
exceptional user experiences by Observelite.


